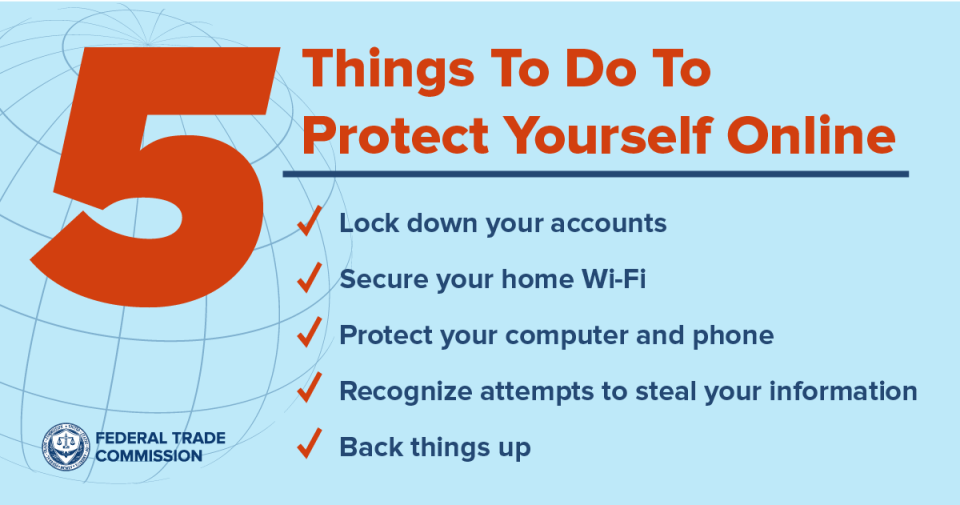
Your online accounts, computer, and phone hold a lot of your personal, financial, and health information. Information that’s valuable to you — and to scammers who try to steal it. Here are five things to do to keep hackers out of your accounts and your personal business.
1. Lock down your online accounts
Your password is the key to all the personal information in your account. Make it long. Avoid common words. And don’t re-use it.
If it’s available on your accounts, turn on multi-factor authentication for an extra layer of security.
2. Secure your home Wi-Fi network
Your wireless network is the hub that connects your devices. To protect it from hackers
- encrypt it
- change your default passwords
- and keep it up to date
Here’s detailed advice about how to secure your home Wi-Fi network.
3. Protect your computer and phone
Once your home Wi-Fi network is secure, focus on protecting your devices.
If you use a computer to go online, make sure your security software, operating system, and Internet browser are up to date. Turn on automatic updates to keep up with the latest protections.
Keep your phone up to date, too.
4. Recognize attempts to steal your personal information
Scammers try to trick you into giving them your personal information. They’ll pretend they’re with an organization you know well — like Apple or Amazon — and make up a reason they need some info from you. They’ve also impersonated FedEx, the Postal Service, the Social Security Administration, and the FTC.
If you get a phishing email or text message, report it.
5. Back things up
Back up important information you have on your computer and phone. That way, if something does happen, you can recover your information. Here’s how to back up your computer and your phone.
Concerned about protecting your privacy online? Check out our guide to protecting your privacy online.

Thank you for the information but if you find someone that is trying to get something in my name than what company should be alert 📢 because I live in a shelter and don't have any money to pay for someone else and I have been contacted by the same company that you talk about and all I do is delete the entire email Thank you very much
I’m very confused as to why your company claims to help consumers when we have reached out begging and pleading for help for almost 4 years now